By Elizabeth Hawk & Cameron Upton
“Ransomware is a type of malware used by cyber criminals who encrypt files and then extort money in return for unlocking these files”[1]. The ransoms demanded are most often in the form of bitcoin or other forms of cryptocurrency which allow for the sender and demanding party to remain anonymous. In the past, ransomware targeted individuals regularly, but in more recent year’s criminals have the ability to encrypt much larger files and have moved forward to larger companies. In this study the focus will be on one group in particular that has emerged in more recent years in targeting major companies and healthcare services. The group chosen to focus on is Hunters International. They are a ransomware-as-a-service (RaaS) group that have attacked large corporations within the last 5 years. Hunters International emerged in October of 2023 following the FBIs takedown of the Hive Ransomware group. For some background, Hive was one of the most active ransomware groups at the time the FBI hacked into their infrastructure to take them down. The Hive group had a distinct malware code that was not seized and is believed to have been transferred to Hunters International. Hunters International has made clear they are not a rebrand of Hive, while having the same motives and utilizing roughly 60% of the same coding and infrastructure. When looking for information on Hunters International on the Tor Browser, the website and corelating information was found on Ransomwatch where the group was shown as active, with leaks being as recent as April 24th, 2024. Hunters International has taken hundreds of company's information along with personal information of their customers, in this case the following three were focused on: Mid-South Health System, Covenant Health Care, and Bradford Health Care. These were chosen based off of the size of the attack, the time of the attack, and the type of health care service provided. This allowed for a smaller scope to focus on, while providing an array of data regarding what is released within an attack and the size of such attacks.
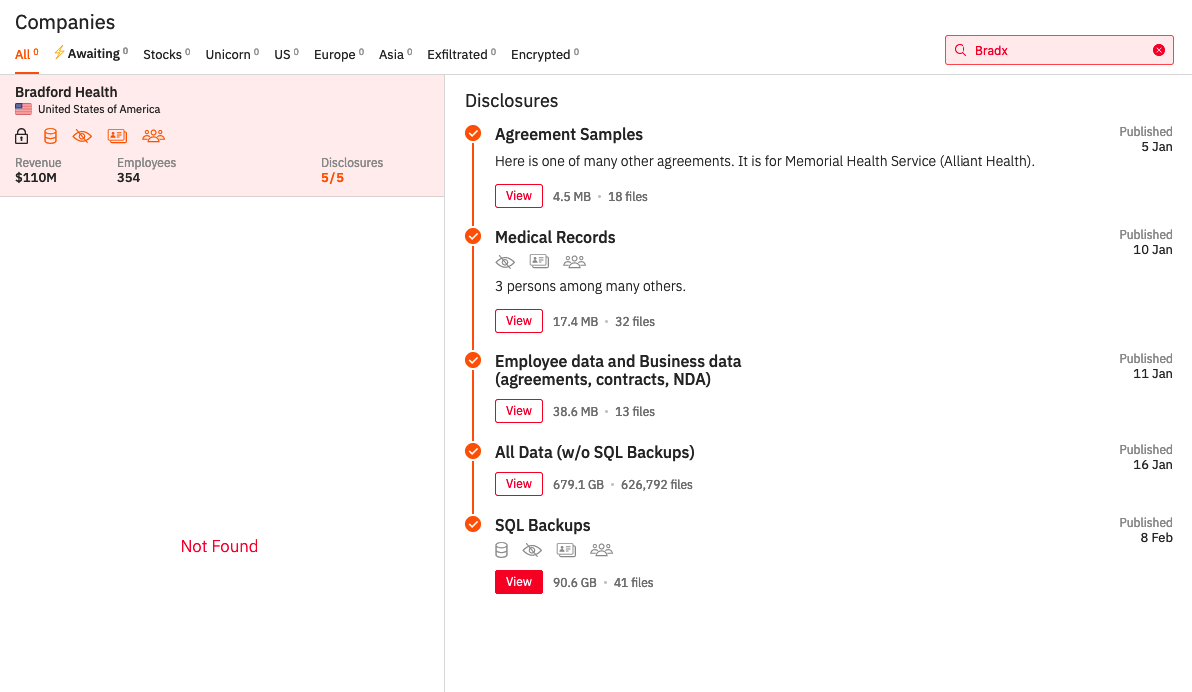
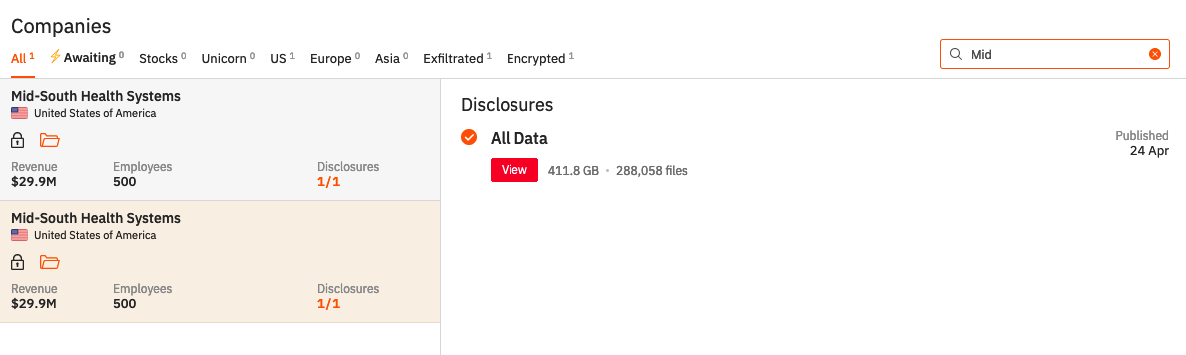
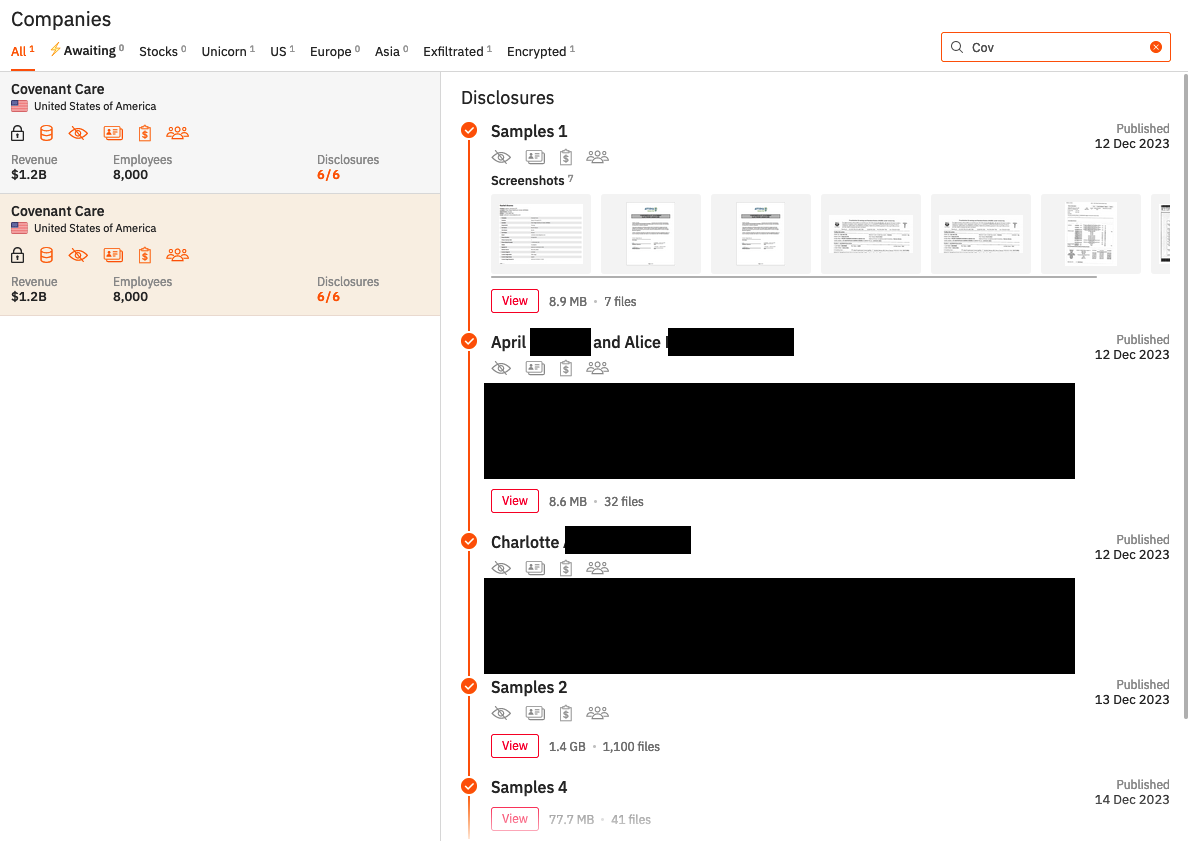
Mid-South Health System, located in Paragould, Arkansas, is a private mental health and substance abuse treatment center. This system is now under Arisa Health and provides in-patient and out-patient treatment. Mid-South Health System had until April 24, 2024, to make the ransom payment before all of their data was leaked rather than small leaks as discussed previously. It is unknown at this time what data Hunters International has and will be leaking.[2]Covenant Health Care is the second victim we chose to focus on and owns nursing facilities and home health agencies in California and Nevada.[3] Covenant Healthcare is one of the larger healthcare attacks with the revenue showing at $1 billion. Around November 14, 2023, Covenant Health Care noticed strange activity on their computer network and identified that certain copies were copied from their system. This company has released a statement to their patients and other individuals who may have been affected discussing what had occurred. Covenant Health Care states that the hackers were able to obtain access to the system through two employee email accounts. It is believed that the information stolen includes “names, addresses, dates of birth, social security numbers, driver's license numbers, medical information/treatment, prescription information, medical insurance information, and more.”[4] The ransomware demand is still occurring and has been occurring since 2023 with slow leaks of different patients' information being released at different times. Bradford Health Services is a company that owns multiple drug and alcohol addiction treatment centers. The company is based in Tennessee but operates in multiple states including Alabama, Mississippi, North Carolina, and Arkansas. On January 4, 2024, Bradford Health experienced a breach that caused an operations blackout and data being stolen and leaked. There were 354 employees at Bradford Health whose data was involved in the leak, causing a revenue of around 110 million dollars.[5] All of the data was leaked on February 8th, 2024. As of late April 2024, all data taken from Bradford Health was leaked by Hunters International.
Before Hunters International rose to becoming a larger ransomware group, Hive was a ransomware group that had become a major player in the ransomware realm since June 2021 when they emerged. This group had attacked more than 1,500 victims and extorted more than $100 million from these attacks.[6] Hive’s victims hail from 80 counties and they attacked sensitive companies including hospitals, school districts, financial firms, critical infrastructure, and more[7]. Hive is a ransomware-as-a-service model that allows group members to use it as they desire. They use common ransomware tactics to breach victims’ devices, including phishing emails, VPN credentials, and utilizing vulnerabilities on external-facing assets[8].This group copies and encrypts files, then they ask for a ransom for the victim to be able to have their files decrypted and the files copied not to be published on their dark web website. If the ransom is paid, it is then split where the developers of the code get 20% of the profit[9]. Hive was taken down in January 2023 by the Federal Bureau of Investigation after they had been penetrating Hive’s computer networks since July 2022. The FBI had retrieved decryption keys to offer to active victims worldwide, along with distributing them to those who had previously been victims of this group. Finally, the department in coordination with German law enforcement and the Netherlands National High Tech Crime Unit, was able to take control of Hive’s servers and websites that the ransomware group used to communicate with its members[10]. While the Department of Justice took down the Hive servers in early 2023, the Department of State announced a reward in February 2024 for any information leading to the identification of any key leadership members in the ransomware variant transnational organized crime group. [11]Hunters International is believed to be a branch of the Hive continuing after the shutdown and utilizing and implementing roughly 60% of the same coding language used by Hive. It is believed that Hive most likely sold their code to Hunters International before the shutdown.
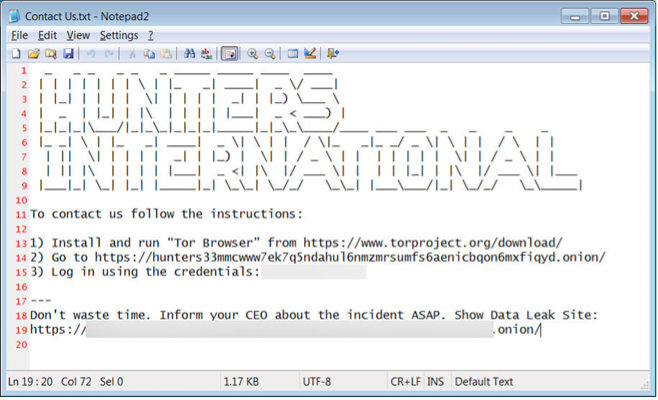
Figure 1. Hunters International Message to Victims[12]
When a ransomware group attacks a company, they go after data including bank records and other personal information. In the case of Hunters International they have a distinct process for their attacks. As seen in Figure 1 Hunters International warns the group they have attacked through a message that shows up on the victim’s screen. This message tells the victim that the group has personal information and has entered their database while also giving instructions on how to get back their data and contact the group for payment. Following the messaging Hunters International then takes to releasing bits of information until payment is made it seems. As seen in Figure 2 in an attack on Bradford Health, the group released bits of information until the deadline was met and they released all the information on Bradford Health. Figures 2 & 3 show the timeline of events utilized by Hunters International when the group partakes in an attack. Firstly, there is proof shown to the victim of the information stolen from them and that Hunters has that information for release if a ransom is not met. Following that, there are smaller releases of information leading up to the final release if ransom is not met or given to the group. In some cases, like the Mid-South Health Systems breach, there is not a timeline of events but rather one large release of information if the ransom is not provided by the deadline.
Figure 2: Ransomware Timelines-Hunters International - Bradford Health
Figure 3: Ransomware Timelines-Hunters International - Mid-South Health Systems
Figure 4: Ransomware Timelines-Hunters International - Covenant Care
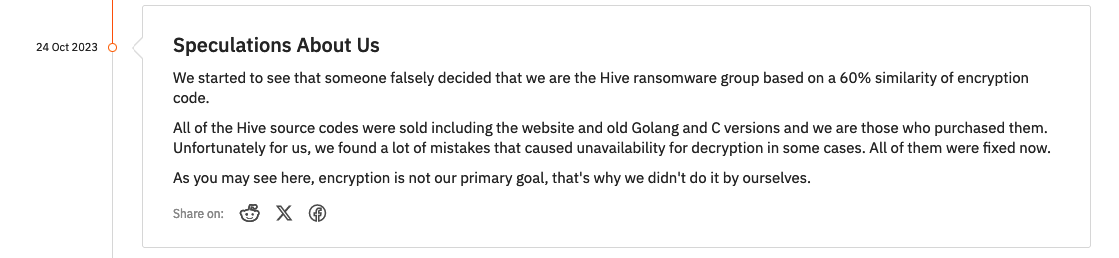
Figure 5: Hunters International Addressing Speculation of Origins
While looking into the breaches of these health services, it can be seen that there are not many news sources covering these breaches. This brings up the larger issue of why these are not being told to the media. It is important for the public to know where these breaches occur as they may be involved, to know how common it is with companies, and how to help protect themselves if this happens where they are the victim. News coverage of these events would help with proper education about when these events occur to individuals. News coverage spreads the word about these events, especially by hitting major news sites and companies could be beneficial for people who never knew something like this could happen to them and have heard about what it is and how to address it if it ever occurs. The extremely limited news coverage is unbeneficial, especially when health services are breached and people's valuable information is being leaked on the dark web, which is easily accessible. The news should be looking into these cases and reporting as much as they can to help not only companies but also individual lives that are impacted by these ransomware breaches daily. A push for news should be enforced by the public so that they are able to get as much information regarding threats to their safety through not only their personal computers but also ransomware attacks on hospitals, education facilities, and other companies that have personal information.
Hunters International is just one example of the hundreds to thousands of ransomware groups working on the dark web. As this is such a large and frequent event that occurs to a wide range of individuals and companies, one way to be able to address it is to keep people informed. As discussed with the news cover, educating individuals about how this occurs and how to help protect themselves is crucial. This would be beneficial to help with possibly lowering the breach rate.
The threat of ransomware on healthcare and healthcare services is an ongoing rising issue. “Ransomware is typically spread through fake emails that have been designed by the hacker to appear legitimate”[13]. “Prior to 2016, healthcare organizations were not thought to be a primary target for hackers, since then they have become easy targets for hackers for two major reasons: 1) the necessity for computer-stored information associated with patient care and 2) the security holes in IT systems”[14]. The first documented case of hospital ransomware was at Surgeons of Lake County in 2012, with similar attacks following in suite. The first few ransomware attacks were not publicized until 2016 when ransomware hackers attacked Hollywood Presbyterian Medical Center. “In this attack staff was able to access patient records, X-rays, and other equipment, or to restore equipment from backup data and was forced to pay the ransom of $17,000 or 40 bitcoins”[15]. Legal experts have determined that there are “four categories associated with ransomware attacks: medical malpractice, data privacy, property, reputation, and cost and expense issues”[16]. The IBM Security Services Cyber Security Intelligence Index detailed events of over 1,000 of IBM Security Services clients in over 133 in 2014, “the findings showed that over 95% of all investigated security incidents were attributed to human error with the most common reason being a user clicked a malicious link or went to a malicious website”[17]
Healthcare has become a major target for ransomware attacks and in response to this it is vital for hospitals and providers to create a plan to properly secure their information. With proper security and planning the healthcare industry is less likely to experience a loss of information in a data breach and a loss of funds due to paying ransoms. The threats that arise with ransomware attacks are so large that as they continue more innocent lives are at risk of losing their information to hackers taking over healthcare services. As seen in the Mid-South Health attack, an ongoing ransomware attack at the time we found it, information regarding patients- from social security to their home addresses- were at risk of being stolen and released to the public on the dark web. Another major issue with the threat of ransomware is that on the dark web this information is available for free, while on the Hunters International website the information stolen was available for download with no purchase. To put a stop to this, hospitals and corresponding healthcare services need to create a plan for such attacks to ensure as little information is taken as possible, and they do not have to pay the ransom.
[1] Spence, Nikki, David P. Paul III, and Alberto Coustasse. "Ransomware in healthcare facilities: the future is now." (2017).
[2] https://rehabs.org/mid-south-health-systems/
[3] https://www.covenantcare.com/notice-of-data-incident/
[4] https://www.happierit.com/knowledge-center/breaches/covenant-healthcare-email-breach
[5] https://www.privacyaffairs.com/hunters-international-attacks-healthcare-facility/
[6] Bushwick, Sophie. “FBI Takes Down Hive Criminal Ransomware Group.” Scientific American, February 20, 2024.
[7] “U.S. Department of Justice Disrupts Hive Ransomware Variant.” Office of Public Affairs | U.S. Department of Justice Disrupts Hive Ransomware Variant | United States Department of Justice, January 26, 2023.
[8] Ovadia, Nadav. “Hive Ransomware Analysis.” Varonis, February 15, 2023.
[9] “Cybercriminals Stung as Hive Infrastructure Shut Down.” Europol. Accessed April 29, 2024.
[10] “U.S. Department of Justice Disrupts Hive Ransomware Variant.” Office of Public Affairs | U.S. Department of Justice Disrupts Hive Ransomware Variant | United States Department of Justice, January 26, 2023.
[11] Reward offers for information to bring hive ransomware variant co-conspirators to justice - united states department of state. Accessed April 29, 2024.
[12] Ilascu, Ionut. “New Hunters International Ransomware Possible Rebrand of Hive.” BleepingComputer, October 29, 2023.
[13] Ransomware in healthcare facilities: The future is now. Accessed April 29, 2024.
[14] Ransomware in healthcare facilities: The future is now. Accessed April 29, 2024.
[15] Ransomware in healthcare facilities: The future is now. Accessed April 29, 2024.
[16] Ransomware in healthcare facilities: The future is now. Accessed April 29, 2024.
[17] Ransomware in healthcare facilities: The future is now. Accessed April 29, 2024.