By Grace Kirkpatrick, Simone Spiller, John McAleer
Ransomware, a type of malicious software that prevents access to computer systems or data until a ransom is paid, has emerged as one of the largest and most devastating cyber risks in today's world. Ransomware attacks have become increasingly common over the last decade, attacking people, organizations, and vital infrastructure. The anonymity provided by cryptocurrencies like Bitcoin helps hackers in the blackmail process, allowing them to demand and collect ransom payments with a slim chance of being detected and identified.
From small enterprises to big organizations, no one is safe from the danger presented by ransomware attacks, as hackers use software flaws, human error, and sloppy cybersecurity measures to access networks and gather sensitive data that is worth being paid for. A successful ransomware attack has devastating consequences, mostly including financial losses, as well as operational interruptions, and compromised data. As ransomware attacks become more and more sophisticated, addressing this growing threat needs a collaborative effort from cybersecurity professionals, policymakers, and individuals to strengthen defenses, improve threat intelligence sharing, and minimize the impact of these cyber threats on society.
The Black Basta Ransomware Operator group is an infamous organization in the world of cybercrime, known for its ransomware attacks on organizations throughout the world. The group's efforts showed a significant rise in the complexity and effects of ransomware attacks and how devastating they can be. The Russian-based group reportedly tallied over $107 million from late 2022 through 2023, extorting an estimated 90 companies, including industrial giant ABB.[1]
The exact origins of the gang known as "Black Basta" are still unknown because, because of areas of the dark web all of them stay unidentified and disguised. It is believed that the gang first began in Eastern Europe or Russia, which are known for enabling cybercriminal companies due to low regulation and a talented group of programmers who are granted immunity because of interconnections and relationships with the Russian government. Many of these groups (like Black Basta) either operate with impunity in Russia or some level of collusion or coordination with Russian agents.[2] The group started gaining more attention in the world of cybersecurity around 2015, as their actions became popular by targeting larger organizations such as construction and US business organizations.
As the Black Basta Ransomware Group grew, so did its strategies and complexity. Their main method of operation is to distribute ransomware, but they also use a variety of infection methods, including phishing emails and hacked remote desktop protocol (RDP) connections. Once within a network, Black Basta uses complex encryption methods to encrypt key information, providing victims with a stark choice: pay the ransom or risk losing their sensitive data. Black Basta has also used other distinct techniques in their attacks, such as disabling the compromised system’s DNS services to complicate the recovery process by preventing it from accessing the internet and deploying a ransomware variant that targets Linux-based VMware ESXi virtual machines (VMs).[3]
Black Basta has proven that it is prepared to change and modify its strategies in reaction to cybersecurity countermeasures. They have a history of working together with other cybercrime organizations, exchanging infrastructure, methods, and tools to increase operational effectiveness and avoid being discovered or compromised. Law enforcement organizations have also increased their efforts to stop ransomware activities and capture those responsible. Cybercriminals such as Black Basta are frequently able to operate with a certain degree of anonymity due to the international nature of cybercrime, which poses difficulties for attribution and prosecution.
Overall, the Black Basta Ransomware Group is an imminent threat in the constantly changing world of online dangers. Given its advanced strategies, global presence, and tendency to attack vital infrastructure, the group presents a serious threat to cybersecurity players everywhere. To properly counter the threat posed by organizations such as Black Basta, efforts to tackle the ransomware problem must involve a multi-pronged approach that combines technological innovation, regulatory measures, and international cooperation.
Typical Victims and MicroTrends
As previously mentioned, Black Basta is known as a Russian speaking ransomware group, and interestingly enough, it seems that most, if not all of their targets, are typically English speaking companies or entities. They typically target entities within the United States, but have also shown interest in countries such as Austria, Canada, the UK, and New Zealand.[4] They use ransomware and the threat of publicly releasing sensitive data to grasp their victims.
A study was done by Trend Micro Research focusing on the time period of April 1st to July 31st of 2022, lines up with the previous claims of typical Black Basta victims. During this time period, it was found that the United States accounted for 43.2 percent of Black Basta victims. In second place for the most attacks within the same country was Austria at 15.9 percent, while all other attacks in multiple different countries accounted for the last 40.9 percent. For reference of this last roughly 50 percent, most of the attacks were in North America, some were in Europe, and a few were in Asia. Some have thought that Black Basta might specifically target the Western hemisphere, however there is not much evidence to support that.[5] In addition to trends in location of Black Basta attacks, this ransomware group doesn’t seem to have strict tendencies in regard to the specific industries it attacks. Some of the industries could be construction, manufacturing, fashion, finance and even retail. Black Basta has a high level of diversity within who their victims are, only focusing on what industries have the most money, leading experts to believe that no industry or sector is safe from possible attacks.
Attack Technique Patterns
It’s been found that Black Basta typically gains access to their victims' servers and data through a phishing email. The phishing emails are the “initial discovery” of the attack. The next stage of the attacks is the discovery stage. This can look like the operators behind the attack using Qakbot, a malware software that specializes in stealing or gathering information.[6] The next stages differ depending on what defenses come up on the infiltrated victim. The next stages could be exfiltration of data, or a general overall execution of data theft. Another stage could be defense evasion. [7]Which is ultimately countermeasures of the ransomware to the security measures of the victim. Obviously, at the end of this terrifying process, the Black Basta ransomware disrupts a computer in its entirety, and it has found a new victim to exploit. Studies show that this is Black Basta’s common strategy of attack, and although there are other techniques, we can only hope they continue to use this one, so people can be as prepared as possible.
Research Methods
To gather our data, we accessed a Tor based news site that held important information on victims of Black Basta attacks between the dates of April 7th, 2024 to April 23rd, 2024. We analyzed the information based on region, industry, revenue, and number of attacks. Additionally, we did a study of study of sorts, a small metastudy, using data from other research to grasp a better understanding of what Black Basta is, why they attack those they do, and how they conduct their attacks. For gathering information on Black Basta’s victims, we read a threat profile published by the Health Sector Cybersecurity Coordination Center[8]. This actually gave us the onion link to Black Basta’s leak site. Black Basta, when gathering its victim’s compromised data, exploits the compromised downloaded files online on their leak site, by offering customers the chance to download files of a company or enterprise if they are willing to pay. The website offers financial, security, client, and many other different types of files to download from your selected company. In real time, you can watch how soon a new company’s data will be published on their home screen page if the company refuses to pay the ransom.
We were curious to know how many attacks black basta had made in the past two weeks, and who they had exactly attacked. We were curious to know if there were any patterns in their targets. To collect the information, we went through the latest compromised companies of the past two weeks. We collected data on their industry sector, their annual revenue (researched through zippia.com and rocketreach.co) , their country of origin, and their Fortune Global 500 status. Most of this data was found through Black Basta’s leak site, while the fortune global 500 data was found through hitting control plus F on Fortune.com’s global 500 list.
Data Analysis
In the past two weeks from April 7th to the 23rd, Black Basta compromised the data of 20 companies. Its targets in order from most recent to least are CINFAB Inc, Siemens, Columbia Pipe & Supply Co., Hanwha Azdel, HYMER, Cavotec SA, Macphie, Fluent, Doyon Drilling, Arch-Con Corporation, Paterson & Cooke, Atlas Container Corporation, Robar Enterprises, Schlesinger law offices, Sermo, The Parklane Group, Numotion, Process Solutions, Rentacrate Enterprises, and GFG Capital. Some of these companies are household names such as Siemens, Hymer, and Hanwha Azdel. Other companies on the list are too small to be widely known, like Macphie Foods, a Scottish food ingredient manufacturer[9] or Schlesinger Law, a small Law Firm out of Florida[10].
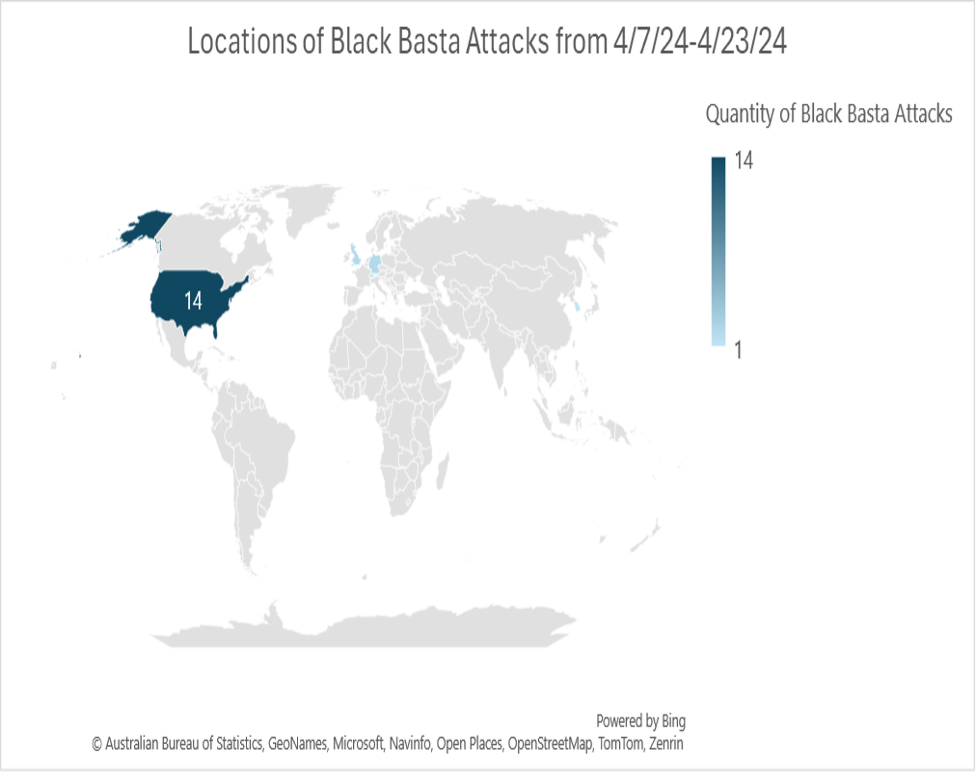
Figure 1. Heat Map of Black Basta Attacks from 4/7/24 - 4/23/24
Using the addresses given on Black Basta’s leak site, we gathered the origin countries of the 20 companies. Fourteen of the 20 companies hacked were American origin (United States) companies. Two countries originated from Germany, Two countries originated from the United Kingdom, one hacked company started in South Korea, and another was from Switzerland. The highest targeted company origin country was by far the United States. Almost all of these countries were also western, with the only outlier (South Korea) holding strong US alliances. This information holds true and steady with what we already know about the nature of Black Basta; that it particularly targets Western and Western alliance companies8. The heat map shows concentration of attacks through saturation of the color blue. The countries mentioned that were only attacked once or twice, are a very faint blue, and almost invisible on the map. The country with the highest number of targeted attacks within the past two weeks (The United States) is the darkest blue of the entire map.
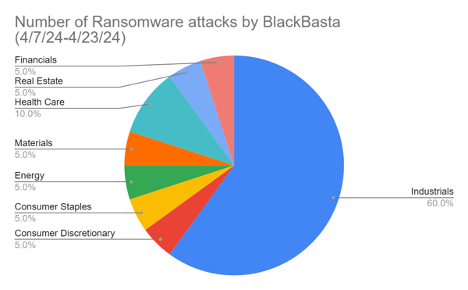
Figure 2. Pie Chart Displaying Sectors of Targeted Companies
The next factor we were interested in was what sectors were most affected by Black Basta’s ransomware attacks. To do this, Black Basta’s leak page actually had information from the companys’ home pages in regards to its business practice type. The data was gathered into a google spreadsheet, but many of the companies listed had such specific services that it was hard to put all of the companies in a sector. To ease this classification, we used the Global Industry Classification Standard created by MSCI and S&P[11]. It is often used for investors to help with the definition of industry, but here it will be used to discern which sectors are most targeted. Out of the twenty companies, eight sectors were targeted; industrials, consumer discretionary, consumer staples, energy, materials, health care, real estate, and financials. With the large amount of hacking health care groups, it was surprising to note that the highest hacked company sector was industrials, although the health care sector was the second most compromised of the affected sectors. The industrial sector was heavily targeted these past two weeks of April seventh to the twenty-third, with twelve total ransomware attacks from black basta, while the second largest sector, health care, only had two. The six other sectors only had one attack maximum throughout the two week period. This may show that Black Basta heavily targets Industrial companies, but still diversifies its other targets.A reason that Black Basta may be targeting the industrial sector is due to its often higher grossing revenues. Companies that sell capital goods, commercial and professional services, and transportation are always highly needed by the market, and therefore good targets for ransomware attacks.
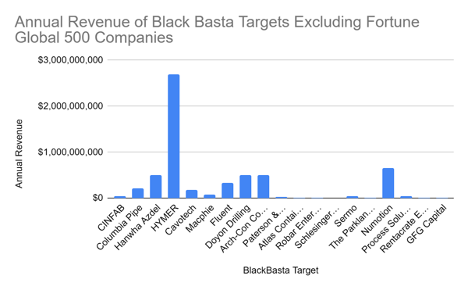
Figure 3. Annual Revenue of Targets
Figure 4. Annual Revenue of Non-Fortune Global 500 Targets
To find the revenue of the companies we used data on annual revenue from Zippia.com, zoominfo.com, as well as rocketreach.co. Fortune global 500 is a ranking of the top 500 global companies ranked by their annual revenue[12]. These are prominent companies with high yielding sales. It is disturbing to note that two out of the twenty companies hacked were fortune global 500 companies; Siemens and Hanwha Azdel12. Black Basta’s targets from this sample group are not just small businesses. Almost all corporations attacked are multimillion dollar companies. Two of the corporations listed are billion dollar companies, with Siemens leading the annual revenue with 77 billion dollars, and Hymer close to three billion. Siemens’s revenue was so much that it threw off the visuals of figure 3, so another chart without fortune global 500s was created, to show the many different revenue targets. Figure three may be misleading due to the fact that its range of the y-axis is so large. It is important to note that the revenue here had a range of 0 to 3 billion dollars.
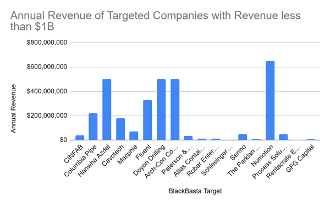
Figure 5. Annual Revenue of Targets with less than $1B
The incredible revenue range of Black Basta’s targets show that they can easily attack any type of company whether it be high grossing or a small family business. Their main target is industrial companies with multimillion dollar annual revenues, to yield a high ransom payment if the victims choose to pay out.
Conclusion
Ransomware is one of the most dangerous weapons known to man. Roughly 73 percent of all companies that are attacked by ransomware end up paying immense amounts of money to retrieve their data.[13] Black Basta has been a major player in the ransomware world for a few years now, and it doesn’t look like they’ll be leaving anytime soon. By the end of 2023, Black Basta had already made roughly 107 million dollars in profit. That number can only go up as of now. The one good thing about this data, is that companies and individuals can use that information and prepare themselves to the best of their abilities. Black Basta is not some group of people wearing black hoods in a dark basement, it is a group of intelligent cyber experts who want money and are willing to infiltrate anything to get it.
Bibliography
Ani Petrosyan, and Aug 31. “Global Ransom Payers That Recovered Data 2023.” Statista, August 31, 2023. https://www.statista.com/statistics/700894/global-ransom-payers-recovered-data/#:~:text=In%202023%2C%20nearly%2073%20percent,over%20the%20past%20few%20years.
“BLACK BASTA: ANATOMY OF THE ATTACK.” infoblox, May 19, 2023. https://blogs.infoblox.com/threat-intelligence/black-basta-anatomy-of-the-attack/.
“Black-Basta-Threat-Profile.Pdf.” HC3 Threat Profile, 2023. https://www.hhs.gov/sites/default/files/black-basta-threat-profile.pdf. (citation 8)
Editors, Fortune. “Global 500.” Fortune, December 18, 2023. https://fortune.com/ranking/global500/.
“Fort Lauderdale Personal Injury Lawyer: Schlesinger Law Offices, P.A.” Schlesinger Law Offices, March 20, 2024. https://schlesingerlawoffices.com/.
“GICS® - Global Industry Classification Standard.” MSCI, 2024. https://www.msci.com/our-solutions/indexes/gics.
“Macphie Ltd: Foodservice and Bakery Solutions.” Macphie, March 13, 2024. https://www.macphie.com/.
“Ransomware Spotlight: Black Basta.” Security News, September 1, 2022. https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-blackbasta.
Reinke, Jeff. “Breaking down Black Basta’s Big Year.” Manufacturing.net, February 8, 2024. https://www.manufacturing.net/cybersecurity/blog/22886430/breaking-down-black-bastas-big-year.
Staff, Adlumin. “The Need to Know: Black Basta Ransomware Gang.” Adlumin SaaS Security, November 16, 2023. https://adlumin.com/post/the-need-to-know-black-basta-ransomware-gang/.
“Threat Intelligence Black Basta Ransomware.” Quorum Cyber . Accessed April 29, 2024. https://www.quorumcyber.com/wp-content/uploads/2023/04/QC-BlackBasta-Ransomware-Report-TI.pdf.
“Who Is Black Basta?” Who Is Black Basta? Accessed April 29, 2024. https://www.blackberry.com/us/en/solutions/endpoint-security/ransomware-protection/black-basta.
[1]Reinke, Breaking down, 2024
[2]Adlumin SaaS Security, The Need, 2023
[3]Blackberry, Who Is, 2024
[4]Office of Information Security, Black-Basta, 2023
[5]Quorum Cyber, Threat Intelligence, 2024
[6] Infoblox, Black Basta, 2023.
[7] Infoblox, Black Basta, 2023.
[8] HC3, Black Basta, 2023.
[9] Macphie Ltd, Macphie, 2024.
[10]Schlesinger Law, Fort Lauderdale, 2024.
[11] MSCI, Global Industry, 2024.
[12] Editors, Global 500, 2023.
[13] Statista, Global Ransom, 2023.