By Cathryn Cotten & Joaquin Carrasco
Covid-19 has had lasting effects on the world with its impact on societal, infrastructure, and political landscapes. One of the more notable consequences has been the increase in ransomware attacks. These attacks are usually targeted toward certain companies, industries, or sectors. Ransomware is a form of malware that is evolving continuously as time goes on.[1] The goal of ransomware attacks is to encrypt files with hostile software on a device making it so those files and device cannot function properly.[2] Victims of ransomware attacks are then forced to pay ransom to reclaim their data and decrypt their files.[3] Ransomware attacks have been around globally since 1989 when the first ransomware attack occurred.[4] Email attachments, pop-ups, and messages are some examples of the most popular forms of ransomware.[5]Since 1989 ransomware has evolved and become more on the rise in recent years with attackers becoming more sophisticated and educated on what will work to hack into systems. For example, according to an article by Clare Stouffer it is more likely for a cyberattack to bring down F-35 jets than missiles.[6] This knowledge furthers the idea that ransomware should be studied and understood by a wide range of people. It is impertinent for people to gain more knowledge in ransomware to protect themselves and understand when their data may be at risk. In 2020 there was a worldwide pandemic of coronavirus (COVID-19) which spread rapidly and provided criminals with the opportunity to exploit cybersecurity vulnerabilities and create multiple cyber-attacks targeting health care services.[7] Since COVID-19 the FBI reported a 300% increase of ransomware related cyberattacks.[8] This blog post aims to uncover knowledge connecting ransomware attacks and COVID-19 within the United States analyzing data from the years of 2019-2023 respectively.
In December 2021, following the peak of COVID-19, Anthony Minnear and Friedo Herbig discuss the overall cybercrime threat of ransomware to hospitals and healthcare services in general during the pandemic. During COVID-19 there were lockdowns globally with many people working ‘remotely’ from home. This aided in facilitating an environment where cyberattacks were on the rise given the fact that secured databases were then being accessed at home and more vulnerable to hackers. Additionally, cyber attackers are always keeping up to date on worldwide news and given the global pandemic they took advantage of the influx of information going out and sent out phishing emails to unbeknownst victims attempting to retrieve informative updates on COVID-19.[9] The approach for research within this study was based on the “desk-top” approach and secondarily used systematic collection, gaining resources from secondary data and previously published works. Minnear and Herbig aimed to collect as much information on the topic and review accordingly to discuss and exploit the causes of cyberattacks during COVID-19 and find combatting measures for such crimes.[10] The threat of ransomware was at an all-time high with growing sophistication and levels of innovation within ransomware as early as April 2020.[11] Within 2020 following April there was an obvious and extreme rise in cyberattacks involving ransomware creating a global surge of ransomware attacks by 102 percent between May 2020 and May 2021.[12] There was additionally a rise in profitability from ransomware attacks increasing their probability of occurrence and Ransomware-as-a-Service further encouraged this.[13] For example, there was a rise in money collected from phishing scams from 2020 to 2021 summing to a raise in price by $35,000.[14] Fileless attacks occurring in early 2021 was another complex threat development causing harm to hospital and healthcare service sectors due to their under-funding and insecurity creating unpreparedness for ransomware cyberattacks.[15] It should be noted that pre COVID-19 hospitals and medical facilities were targets for hackers and ransomware groups because of their vulnerability regarding cybersecurity measures and sensitive data of patients.[16] Outdated systems and limited cybersecurity budgets seem to be the biggest cause for this and as ransomware attacks increased during the pandemic they further struggled to defend against the breaches in security. Countries with underfunded healthcare systems and poor cybersecurity measures struggled the most during the rise in cybersecurity attacks as regions in South Africa, for example, were highly vulnerable to phishing attacks and couldn’t focus on safeguarding patient care due to lack of funds and security. In addition to an increase of ransomware attacks, in general, during and after COVID-19, the ransom prices increased at an exponential rate. From March 2020 to May 2021, it was reported there was a 10 percent increase in the cost of data breaches across all sectors furthering the need for increased security and funding to halt ransom attacks. (cite 11) Ransomware in addition to creating an issue for hospitals and their victims creates an ethical issue of “to pay or not to pay”. Minnear and Herbig note that victims in certain situations pay ransom purely to get their data back even though law enforcement discourages making such payments. (cite 11) Following the analysis of resources the study concludes hospitals vulnerabilities to ransomware are due to COVID-19 exacerbating vulnerabilities making healthcare an easy target and the lack of IT within cybersecurity in hospitals. The recommendations to solve this issue in the future are to increase cybersecurity measures to protect patients' data, focus on cyber-resilience, provide awareness training to staff, continuously backup systems and update them accordingly monitoring threats continuously.[17] This research analysis helps create a better understanding of why COVID-19 affected medical centers so broadly and what can be done in the future to retaliate future ransomware attacks.
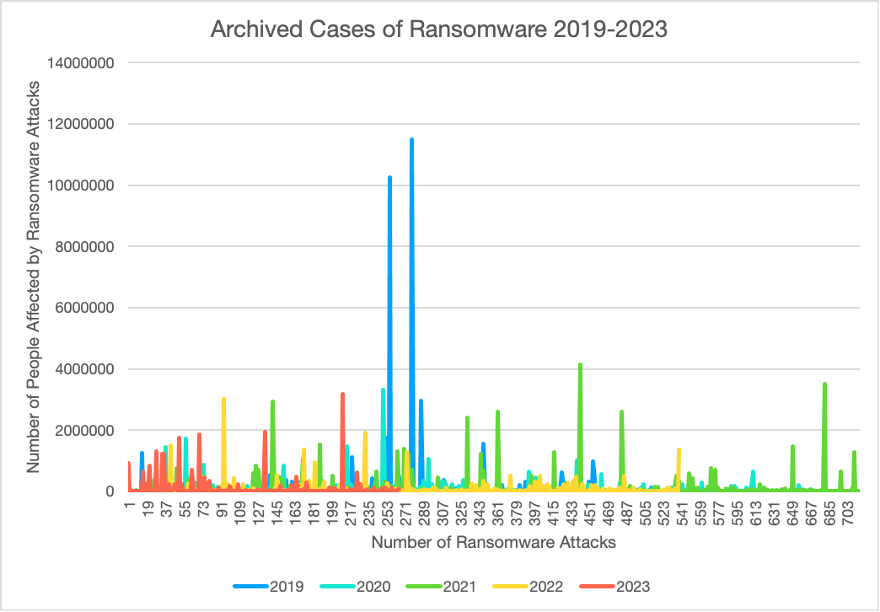
In our data, from the U.S. Department of Health and Services archives, we were able to gather that in 2019 we had the most people affected by ransomware attacks.[18] This date is significant since that was the start of the Covid-19 pandemic and lots of unknowns were at play. Most of the world and most countries have not experienced mass ransomware attacks that attacked infrastructure or the medical sector. These cases were especially targeted to the medical sector in which the people affected had medical records stolen or were held hostage without their knowledge. These cases led to massive reform in governments and the talks of ransomware prevention that we mentioned earlier in the blog. We can also notice that 2021 had the biggest surge in the number of archived cases of ransomware. This data was in conjunction with more than 500 million ransomware attacks that happened in the first half of 2021. This data also shows an overwhelming increase in ransomware attacks between the years 2020 and 2021.[19] The data shows a massive decrease in the number of ransomware attacks in the year 2023. This can be heavily contributed to the leaps in efforts made to combat ransomware attacks and the awareness that countries, governments, and entities had to detect and prevent their data from getting leaked. Of the two spikes in 2019, we were able to see that these two spikes were exclusively targeted at big insurance companies that are in the medical sector.
The data strengthens our initial hypothesis that there are trends between the correlation between the number and increase in attacks during the COVID-19 pandemic to where we are now, which was a direct result of all the attacks.
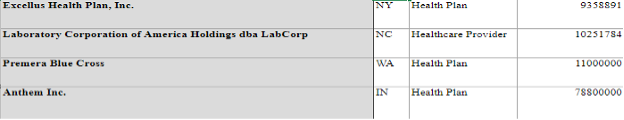
From our data, we can see the categories that lead to the ransomware attack origins. From this, we are better able to see how these groups were losing their data or their consumer's private information. This is key in interpreting how large businesses or large groups such as hospitals became so vulnerable during a crisis such as a global pandemic as something tiny like improper disposal can lead to a company's files being lost. Often it would be user error. For example, in one case, AppleCare reported that an employee of its business associate had inadvertently mailed the protected health information (PHI) of 512 individuals to the wrong recipients. The PHI involved included names and financial information.
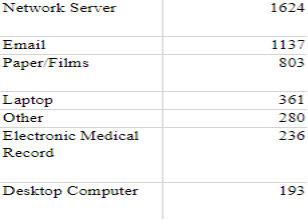
This snip of data also guides us in showing us the most frequent ways they would gain access to and what they utilized to gain private information. Once entering the infrastructure of a entity, they would use these “roads” to further get information. All of this data is critical to understanding the trends, the causation of these trends, and seeing the connections so that we as consumers and citizens can identify and approach future scenarios with more tools to solve an issue at hand.
A recent survey on ransomware early detection was published in February of 2024. Within this survey the publishers analyze research on ransomware early detections to better understand how to catch hackers connected to ransomware before they attack vulnerable systems.[20] Ransomware attackers have recently been attacking larger companies and corporations including commercial companies, energy facilities, government departments and as previously discussed, medical centers. The goal of Ransomware early detection is to identify and intercept ransomware propaganda timely to prevent data compromise and financial loss.[21] Ransomware early detection utilizes methods including behavioral analysis, anomaly detection and machine learning algorithms.[22] From 1989-2009 ransomware was in its “Germination period” meaning the attacks were up and coming, slowly evolving before gaining popularity as in modern times.[23] 2010-2016 marks the “Activation period” of ransomware pertaining to the growth of phishing, spam emails and the creation of Ransomware-as-a-Service.[24] The “Explosion period” of ransomware can be connected to the years of 2017-present due to ransomware’s continued growth and expansion through technology advances and system evolvement.[25] These dates are notated within this study and further explain the idea that ransomware is on the exponential rise and continues to grow. The different early detections for ransomware include the following: behavioral/dynamic analysis, network activity-based detection, API-based detection, Windows-events based detection, data centric/ file-based detection, signature/ static analysis, opcode-based detection, byte sequence-based detection, PE header-based detection, file activity analysis, API calls, hybrid analysis, access control detection, image processing and decoy techniques.[26] While there is a lack of ransomware datasets for researchers to study; this analysis provides insight that there are counterattack methods that can be of use. This literature proves there are counter measures that can be taken and implemented towards ransomware attacks even with the influx of cyberattacks in modern times. Post COVID-19 ransomware early detection could be a promising solution to continuing efforts of countering ransomware attacks.
In this blog post we have reviewed the effects of COVID-19 on ransomware, discussed various literature on COVID-19's effect on cyberattacks and solutions to the continuous rise of ransomware, and analyzed our dataset created. There was a significantly substantial increase in ransomware in the year 2020. SonicWall provides data that there was a 40 percent surge of ransomware globally from January 2020 to September 2020.[27] Ransomware begins in various forms from email phishing to file encryption. Danny Palmer notes that in 2021 there were 3 billion phishing emails sent just in one day, however, he explains DMARC (Doman-based Message Authentication, Reporting & Conformance) can aid in preventing those occurrences daily.[28] Additionally, Jai Vijayan states more organizations suffered successful phishing attacks in 2021 than in 2020.[29] This analysis concludes that there is certainly a correlation between the rise of ransomware attacks and COVID-19. Within this blog post we also identified counterattacks for ransomware to include cyber-resilience, cyber specific funding, training personnel on ransomware, updating systems regularly, ransomware early detection, DMARC and monitoring possible threats to security. Scammers are inevitably going to find new ways to attack files, encrypt data and send phishing emails to companies and vulnerable parties to gain ransom. However, informing the public on solutions to this issue is the first step to improving the lives of those who use the internet daily. Protecting your data is impertinent and while after COVID-19 there was a spike in ransomware detection; education on the topic can aid in ensuring there continues to be a decline in ransomware attacks.
Bibliography
Cen, Mingcan, Frank Jiang, Xingsheng Qin, Qinghong Jiang, and Robin Doss. “Ransomware Early Detection: A Survey.” Computer Networks 239 (February 2024): 110138. https://doi.org/10.1016/j.comnet.2023.110138.
Freed, Anthony M. “Ten of the Biggest Ransomware Attacks of 2021.” Cybersecurity Software. Accessed April 30, 2024. https://www.cybereason.com/blog/ten-of-the-biggest-ransomware-attacks-of-2021#:~:text=There%20were%20nearly%20500%20million,at%20the%20beginning%20of%20October.
Juliana De Groot, Chris Brook, and Colin Mullins. “A History of Ransomware Attacks: The Biggest and Worst Ransomware Attacks of All Time.” Digital Guardian. Accessed April 30, 2024. https://www.digitalguardian.com/blog/history-ransomware-attacks-biggest-and-worst-ransomware-attacks-all-time.
Minnaar, Anthony, and Friedo J.W. Herbig. "CYBERATTACKS AND THE CYBERCRIME THREAT OF RANSOMWARE TO HOSPITALS AND HEALTHCARE SERVICES DURING THE COVID-19 PANDEMIC." Acta Criminologica: Southern African Journal of Criminology & Victimology 34, no. 3 (2021): 155+. Gale OneFile: Criminal Justice (accessed April 30, 2024). https://link-gale-com.ezproxy.lib.vt.edu/apps/doc/A696241979/PPCJ?u=viva_vpi&sid=bookmark-PPCJ&xid=09015843.
“New SonicWall Research Finds Aggressive Growth in Ransomware, Rise in IoT Attacks.” Sonicwall.com, October 2020. https://www.sonicwall.com/news/new-sonicwall-research-finds-aggressive-growth-in-ransomware-rise-in-iot-attacks/.
Palatty, Nivedita. “81 Phishing Attack Statistics 2024: The Ultimate Insight.” Astra Security Blog, April 10, 2024. https://www.getastra.com/blog/security-audit/phishing-attack-statistics/#:~:text=Phishing%20email%20statistics%20suggest%20that,attack%20occurring%20every%2011%20seconds.
Palmer, Danny. “Three Billion Phishing Emails Are Sent Every Day. but One Change Could Make Life Much Harder for Scammers.” ZDNET, March 2021. https://www.zdnet.com/article/three-billion-phishing-emails-are-sent-every-day-but-one-change-could-make-life-much-harder-for-scammers/.
Stouffer, Clare. “115 Cybersecurity Statistics + Trends to Know in 2023.” Norton United States, September 2022. https://us.norton.com/blog/emerging-threats/cybersecurity-statistics#:~:text=There%20isn’t%20a%20clear,spear%20phishing%20attacks%20every%20day.
“U.S. Department of Health and Human Services Office for Civil Rights Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information.” U.S. Department of Health & Human Services - Office for Civil Rights. Accessed April 30, 2024. https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf.
Vijayan, Jai. “More Orgs Suffered Successful Phishing Attacks in 2021 than in 2020.” Dark Reading, December 8, 2023. https://www.darkreading.com/cyberattacks-data-breaches/more-orgs-experienced-a-successful-phishing-attack-in-2021-than-year-before.
[1] Cen, Jiang, Qin, Jiang, and Doss. “Ransomware Early Detection: A Survey.” Computer Networks 239 (February 2024)
[2] Cen, Jiang, Qin, Jiang, and Doss. “Ransomware Early Detection: A Survey.” Computer Networks 239
[3] Ibid
[4] De Groot, Brook, and Mullins. “A History of Ransomware Attacks: The Biggest and Worst Ransomware Attacks of All Time.” Digital Guardian.
[5] De Groot, Brook, and Mullins. “A History of Ransomware Attacks: The Biggest and Worst Ransomware Attacks of All Time.”
[6] Stouffer, Clare. “115 Cybersecurity Statistics + Trends to Know in 2023.” Norton United States
[7] Minnaar and Herbig. "CYBERATTACKS AND THE CYBERCRIME THREAT OF RANSOMWARE TO HOSPITALS AND HEALTHCARE SERVICES DURING THE COVID-19 PANDEMIC." Acta Criminologica: Southern African Journal of Criminology & Victimology 34, no. 3 (2021)
[8] Stouffer, Clare. “115 Cybersecurity Statistics + Trends to Know in 2023.” Norton United States
[9] Minnaar and Herbig. "CYBERATTACKS AND THE CYBERCRIME THREAT OF RANSOMWARE TO HOSPITALS AND HEALTHCARE SERVICES DURING THE COVID-19 PANDEMIC."
[10] Minnaar and Herbig. "CYBERATTACKS AND THE CYBERCRIME THREAT OF RANSOMWARE TO HOSPITALS AND HEALTHCARE SERVICES DURING THE COVID-19 PANDEMIC."
[11] Ibid
[12] Ibid
[13] Ibid
[14] Palatty, Nivedita. “81 Phishing Attack Statistics 2024: The Ultimate Insight.” Astra Security Blog, April 10, 2024.
[15] Minnaar and Herbig. "CYBERATTACKS AND THE CYBERCRIME THREAT OF RANSOMWARE TO HOSPITALS AND HEALTHCARE SERVICES DURING THE COVID-19 PANDEMIC."
[16] Ibid
[17] Ibid
[18] “U.S. Department of Health and Human Services Office for Civil Rights Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information.” U.S. Department of Health & Human Services - Office for Civil Rights. Accessed April 30, 2024.
[19] Freed, Anthony M. “Ten of the Biggest Ransomware Attacks of 2021.” Cybersecurity Software. Accessed April 30, 2024.
[20] Mingcan, Jiang, Qin, Jiang, Doss. “Ransomware Early Detection: A Survey.” Computer Networks 239 (February 2024)
[21] Mingcan, Jiang, Qin, Jiang, Doss. “Ransomware Early Detection: A Survey.”
[22] Ibid
[23] Ibid
[24] Ibid
[25] Ibid
[26] Ibid
[27] “New SonicWall Research Finds Aggressive Growth in Ransomware, Rise in IoT Attacks.” Sonicwall.com, October 2020.
[28] Palmer, Danny. “Three Billion Phishing Emails Are Sent Every Day. but One Change Could Make Life Much Harder for Scammers.” ZDNET, March 2021.
[29] Vijayan, Jai. “More Orgs Suffered Successful Phishing Attacks in 2021 than in 2020.” Dark Reading, December 8, 2023.